So it’s been a while since I last posted anything – I’ve been extremely busy with exam season coming up, but I had a bit of spare time so I decided to post something. Expect more regular posts over the holidays, and I hope to revamp the website a bit so it looks cleaner (and […]
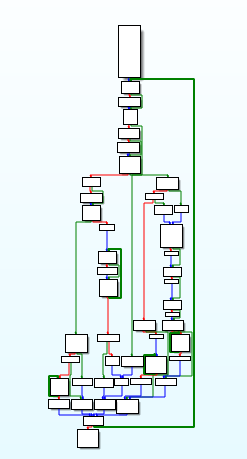
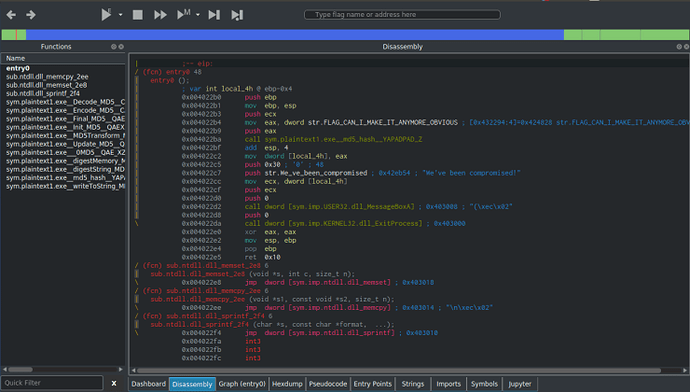
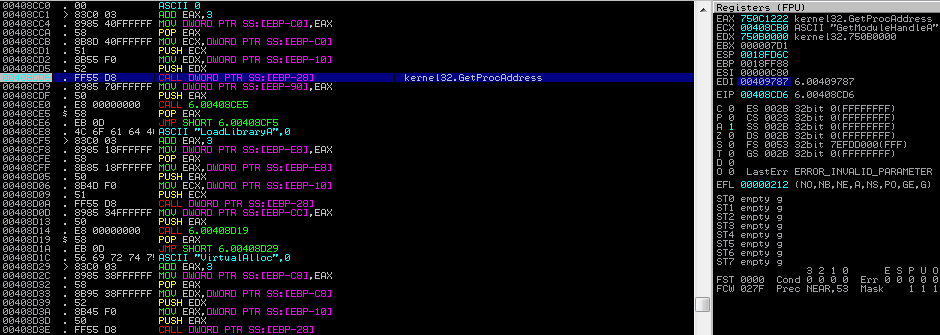
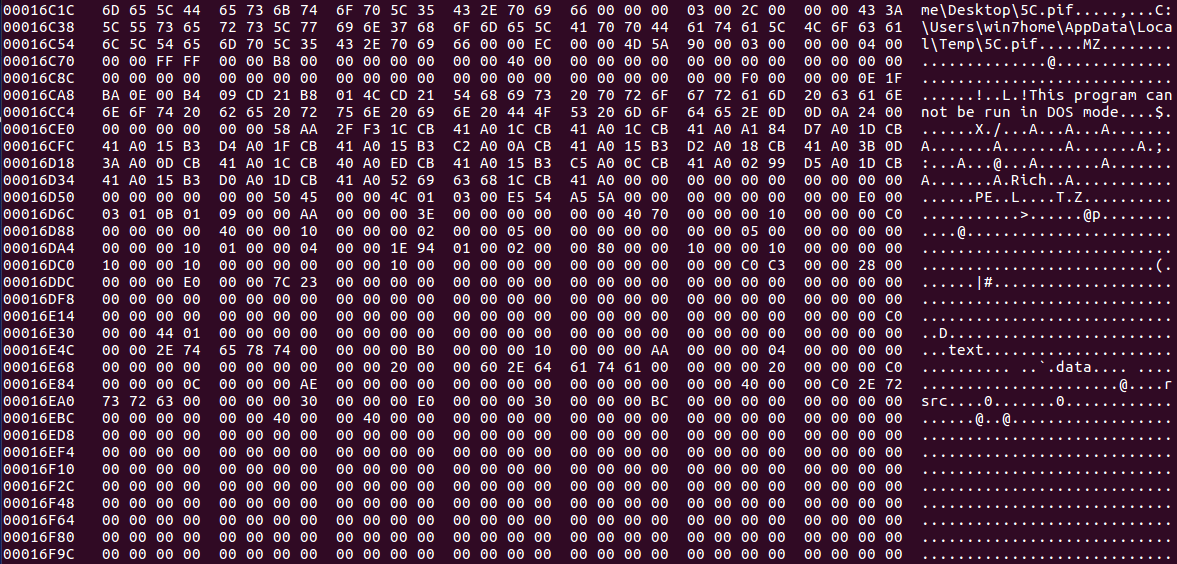
I’ve been wanting to post write-ups about different CTF’s and challenges that I have done, and I’m finally getting round to doing it. And as I’ve been recommended to use Cutter when performing Static Analysis, I decided to kick of the challenge section with some of MalwareTech’s static RE challenges, which you can find here. […]
If you haven’t seen my last post about Hancitor, check it out here as I explain how this binary gets onto your machine through a malicious word document. As always, you can download this sample – both the document and embedded binary – on VirusBay. Let’s begin the analysis! MD5 of Sample: 992f079a832820c61388f753dab1114d I have only had a brief […]
Recently, TechHelpList uploaded a Hancitor Word document to VirusBay, along with an overview of the sites it reached out to, the C2 servers, and the payloads that were dropped by said document. As it seems Hancitor is quite popular for downloading the Pony and ZeusPanda malware (what is it with animals and malware?), I decided to […]
So you may remember I wrote a blog post about the MuddyWater APT group attacking Middle Eastern organizations using their custom Powershell malware (if you don’t, you can check it out here), and I analyzed the malicious VBA macros and the highly obfuscated powershell to figure out what it was capable of. Well, guess what […]
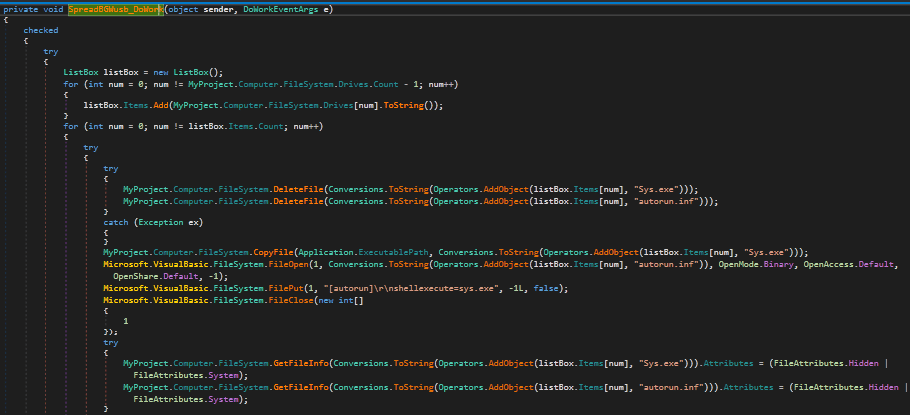
Continuing with the “theme” of the last post, I decided to analyse one more .NET sample for a bit of practice. This time, rather than ransomware, I’m analyzing what seems to be quite an old keylogger titled ReVaLaTioN, which looks to be of Turkish origin. I have not been able to find any blog posts about […]