So it’s been quite a while since my last post, however now that my Beginner Malware Analysis Course is complete, the posts should be more and more frequent, although that obviously depends on the complexity of the samples I am analyzing. If you haven’t checked out my last post on ISFB where we analyzed the […]
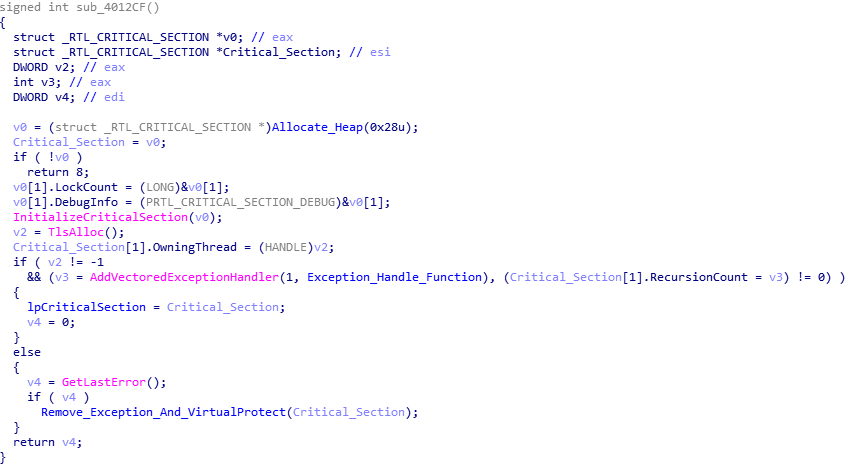
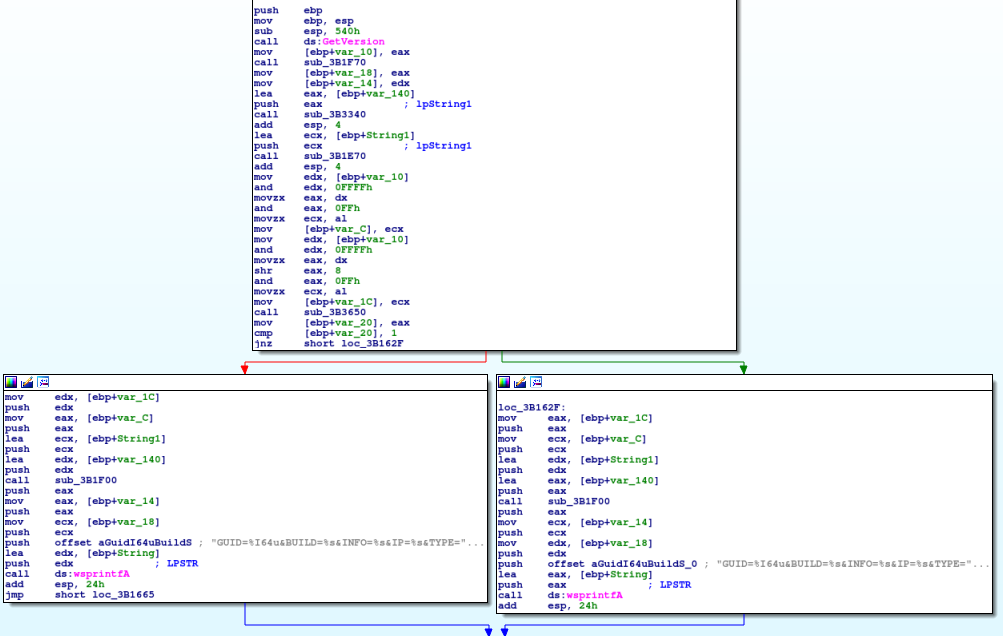
I’m finally getting round to writing this post – for the past few months I have been analysing different versions of ISFB/Ursnif/Gozi to gain a deeper understanding in the functionality of this specific malware. In this post, I will be detailing how to unpack and then analyse the first stage loader executable, and then use […]
As you probably guessed from the title, we are going to be taking a look at Hancitor once again, except this time, I’ll be focusing on the second stage of Hancitor that is dropped as a result of a Microsoft Word or Excel document. I was planning to include an analysis of one of the […]
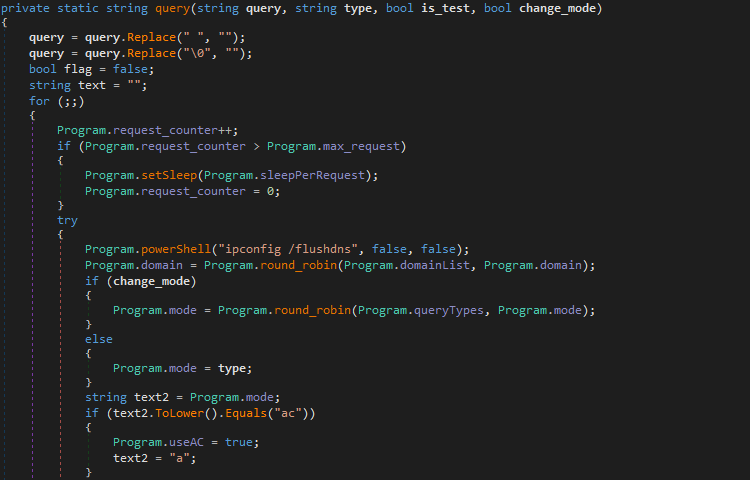
You may remember I wrote about the DarkHydrus APT a while ago, and how their Powershell malware, RogueRobin, was being used to target Middle Eastern organizations and exfiltrate data through the usage of DNS. They have resurfaced after a dormant period, bringing an newly improved and compiled version of RogueRobin discovered by Unit 42, containing […]
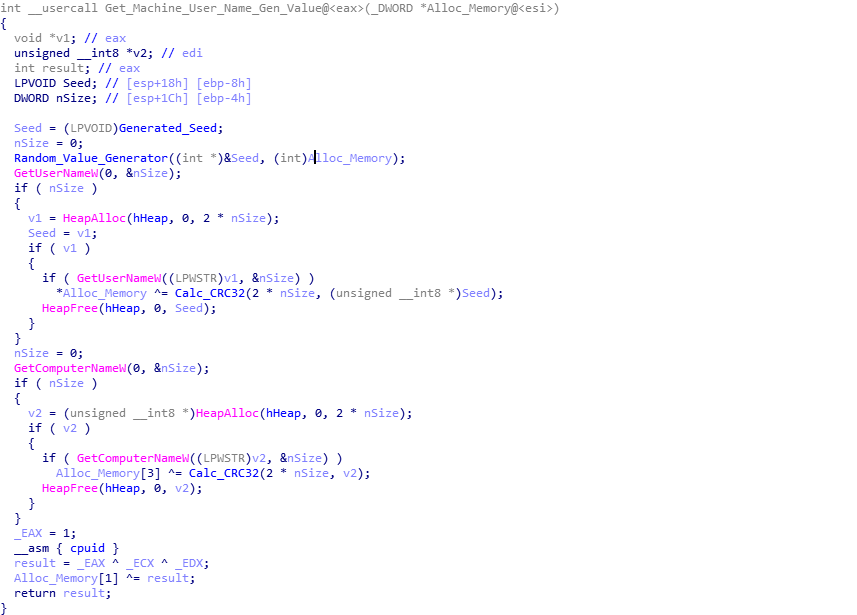
If you follow me on Twitter (@0verfl0w_), you may have noticed a while back that I was analyzing a sample of Ursnif/Gozi/ISFB (which I will refer to as ISFB) and was confused as to how it was able to communicate with its C2 servers through a separate process, without injected DLL’s or process hollowing. I […]
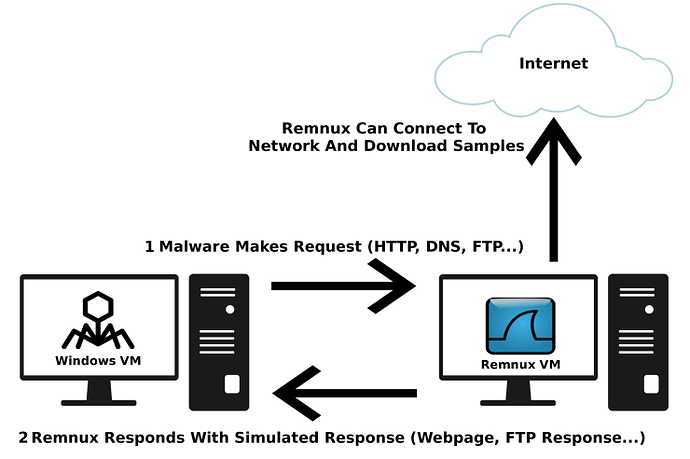
Carrying on with the previous post of getting started with malware analysis (you can find it here), I’ve had requests to do a write up on how I setup my environment for analysis. This guide is also helpful for those of you running a one laptop setup, because that’s what I’m currently using! Obviously you’ll […]